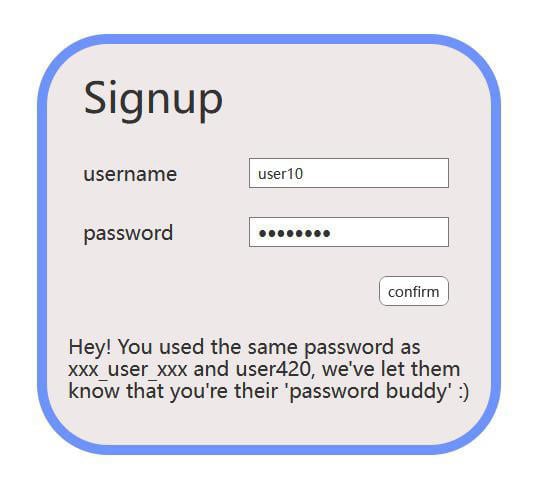
We’ve all been there.
I’ve seen this but with a final message of “Sorry, that password is already in use by user about2getOwned@gmail.com.”
- Login to their account
- Change their password to something else
- Set your password
But what if the password you want to set is already in use?
Refer to my above comment until that is no longer the case.
Fun fact: password controls like this have been obsolete since 2020. Standards that guide password management now focus on password length and external security features (like 2FA and robust password encryption for storage) rather than on individual characters in passwords.
Since 2017 at least; and IIRC years before that; that’s just the earliest NIST publication on the subject I could find with a trivial Web search.
https://pages.nist.gov/800-63-3/sp800-63b.html
Verifiers SHOULD NOT impose other composition rules (e.g., requiring mixtures of different character types or prohibiting consecutively repeated characters) for memorized secrets. Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically). However, verifiers SHALL force a change if there is evidence of compromise of the authenticator.
“Memorized secrets” means classic passwords, i.e. a one-factor authentication through a shared secret presumed to be known to only the right person.
For today’s 10,000 who have never seen it, https://xkcd.com/936/ succinctly explains why the whole mixed character types thing isn’t favoured.
I’m still waiting on an XKCD that references #936 with the fact that we soon as we have reliable, functional quantum computing, all of the passwords from before that point in time will be completely and utterly broken. That the only way to make a password that a quantum computer would have a tough time breaking is if it was made by another quantum computer. Unless of course the comic has already been made and I just missed it, which is a complete possibility because this year for me has been utterly crap.
Some of them are broken by quantum computers, but not all of them. For example, SHA256. You can use Grover’s algorithm to take sqrt(n) steps to check n possible passwords, which on the one hand means it can be billions of times faster, but on the other hand, you just need to double the length of the password to get the same security vs quantum computers. Also, this is the first I’ve heard of a hash that uses a quantum computer. Do you have a source? Hashes need to be deterministic, and quantum computers aren’t, so that doesn’t seem like it would work very well.
Maybe you’re getting mixed up with using quantum encryption to get around quantum computers breaking common encryption algorithms?
Except you can run a dictionary attack on that and suddenly it’s only 4 variables that are cracked way faster than the first password.
Except you can run a dictionary attack on that and suddenly it’s only 4 variables that are cracked way faster than the first password.
I wouldn’t say obsolete because that implies it’s not really used anymore. Most websites and apps still use validation not too dissimilar from the OP, even if it goes against the latest best practices.
Yeah, the most recent one for me was creating a password at lemmy.world
I wouldn’t say obsolete because that implies it’s not really used anymore.
I’m not sure where you heard someone use the word “obsolete” that way, but I assure you that there are thousands if not millions of examples of obsolete technologies in constant and everyday use.
https://www.merriam-webster.com/dictionary/obsolete
no longer in use or no longer useful
Yeah i agree. The best example of this is Linux. To anyone who disagrees, why does a modern operating system require you to use a terminal, or edit config files instead of changing settings in a gui?
Its THE example of ancient software being pushed on to niave techies that would rather have an insecure open source project than a safe, walled garden like Microsoft Windows 11.
Although Windows 11 does have its problems. The chief of which is bogging down the streamlined simplicity with things a normal user wont need like a package manager.
The best example of this is Linux.
Ouch… so, you might want to learn more about technology before commenting in a Technology community…
why does a modern operating system require you to use a terminal
Because a terminal is one of the most powerful modes of interaction ever invented. It can serve as a relatively low-tech UI, but it is also simple enough to be used as a machine interface. It is lightweight, works even when other protocols and interfaces are thwarted by infrastructure issues, because it is simple text, but also meant to be read by a human, it can make for a great interface for logging, you don’t have to guess at which obscure standard (if any) to use to talk to it, compliance with relevant standards is baked into nearly every language ever written, etc.
Try building a system like Kubernetes on graphical UIs… I dare you.
Its THE example of ancient software being pushed on to niave techies
What industry are you working in?! AWS is nearly all Linux. Google Cloud is nearly all Linux. Android is Linux. Hell, even Microsoft finally relented and is now strongly supporting their Windows Subsystem for Linux (WSL) because it’s necessary for supporting modern cloud applications.
that would rather have an insecure open source project than a safe, walled garden like Microsoft Windows 11.
Okay, this has to be a troll… right? This is a troll? Please tell me you can’t be serious.
I know it can be hard to have your ideas quedtioned, but at least try to be civil. I never questioned your intentions, yet youre acting like im crazy. A walled garden is obviously more secure than an open source project because nobody can even see the code to find vulnerabilities in it. There is a reason why Android is moving further and further away from open sores code.
What industry are you working in?! AWS is nearly all Linux. Google Cloud is nearly all Linux. Android is Linux. Hell, even Microsoft finally relented and is now strongly supporting their Windows Subsystem for Linux (WSL) because it’s necessary for supporting modern cloud applications.
I understand that you like horses. You ride one every day, and you might have evwn named your horse. The fact is that its time to buy a car. Notice i said buy. Quality software costs money, and always will. Its time to move into the future with the rest of us.
the terminal is simple
Yes i agree. Throwing rocks is also simpler than firing a gun, yet modern militaries arent training slingers anymore. Ive developed games using Windows exclusivley (for a lot of money i asure you) and ive never once had to use a terminal ever. I literally just have to email my source code to my boss, and he compiles it. I have no need to know how, because its not my problem. Theres no need to use a terminal when i have Visual Studio and Outlook. If you want to be a cool hackerman you can, but id rather use something thats intuitive and works.
I think anyone who uses Linux is stuck in the past. Communism doesnt work either, bucko.
I know it can be hard to have your ideas quedtioned, but at least try to be civil. I never questioned your intentions, yet youre acting like im crazy.
I think that’s all you. I have never suggested that you are crazy. I suggested that calling Microsoft software “safe” as opposed to Linux which is, “insecure,” sounds like trolling. But that’s because it sounds like trolling. No crazy stated or implied.
A walled garden is obviously more secure than an open source project because nobody can even see the code to find vulnerabilities in it.
You should learn more about the world of software. Seriously. Security experts have been reasonably unanimous in their support of the “Many Eyes Make All Bugs Shallow” approach to software security for decades, even while they have criticized it as a mantra that ignores the flaws in a presumption of open source software security.
But just to put it in a simple logically sealed box: Microsoft’s source code has been leaked several times, and of course, bad actors probably have gained access to it throughout the years without such public knowledge. This means that the fundamental difference between Microsoft’s proprietary codebase and open source codebases is not, cannot be the availability of source code. Rather, it is the ability for independent groups to review the code on an ongoing basis.
When the only difference is independent review, the only possible result is higher security.
I understand that you like horses. You ride one every day, and you might have evwn named your horse. The fact is that its time to buy a car.
None of this constitutes a logical refutation to the examples I provided, which are critical components of modern software development and deployment.
Source: I’m a professional software release engineer who has worked with many of the world’s largest corporations.
Quality software costs money
For starters, this is unfounded cargo culting. There is no evidence for this at all. I can point to dozens of very expensive piles of crufty old software that no one should ever go near, and also to some free software that is literally foundational to the modern software world.
Money has nothing to do with the quality of software, but you’re also mistaken if you think open source software is free. You can pay IBM millions of dollars for a suite of enterprise-ready open source software. Most of the cost in such software is rarely the software itself. It’s services, support, training and customization.
Throwing rocks is also simpler than firing a gun, yet modern militaries arent training slingers anymore
But they are succeeding wildly by using largely open source software running on open hardware for drones, networking, battlefield analysis, logistics, etc.
People should be made aware of all the tools available to properly manage tons of passwords. Not even going too deep into “passkey” stuff or any modern shenanigans, but a password manager used to generate random passwords for each separate sites is such a simple step.
For those wanting to play this as a game, there is this wonderfully fiendish website.
https://neal.fun/password-game/
Rule 13 Your password must include the current phase of the moon as an emoji.
I got stuck on the chess one. Used to think I was pretty decent at the game. After a few tries I gave up and tried a few websites that claim to be able to solve it and none found the “correct” move.
“Chessify” on Android worked for me (also has the advantage that you just take a picture, instead of setting up the position by hand). Unfortunately 1 minute later the game gave me a chicken that I had to keep fed with worm emojis, so I created a stockpile of worms for the chicken and it died of overfeeding. I rage quit the game on the spot.
“Sorry, that password is already in use” ruins it for me. That’s not a realistic message to receive.
Maybe “Your password cannot be one you’ve used previously”.
Should be: “your password cannot be one of your last 24 passwords”
At my work they wanted better security, and made the rule of minimum 12 characters, must include all sorts of numbers, special characters, etc, no previously used password and it must be changed every month, 3 attempts then the account is locked and you have to call IT.
The result was that people wrote their passwords on post-its on the screen, so it led to worse security overall and they had ro relax the rules.
Especially for those places that want your password changed every two weeks.
If they want to play that game - the calendar date becomes part of the password. It’s never the same, but you can always work it out!
Or just append a letter that increments every time you change your password, and keep a note of what the current letter is.
Passworda
Passwordb
Passwordc
…When your z password expires, just wrap back around to a.
Should say by who. :)
deleted by creator
Unfortunately a lot of jobs require passwords and they use outdated security processes, forcing people to have the old fashioned “must have uppercase, lowercase, number, and special character & you have to change it every 3 months for no reason” passwords instead of the stronger (and less annoying) alternatives.
i signed up at mba.com and it wouldn’t let me use a password because it contained a semicolon which wasn’t on the approved list of special characters, and then - get this - because I tried too many times to create a password - locked me out because I had “too many failed attempts”
Sounds like it’s prime time for a SQL-injection
that’s exactly why a password manager works. there’s a generator that you can configure to meet requirements
Those requirements drive me crazy, especially because they’re all against NIST recommendations. Someone thinks they make passwords more secure but they have the opposite effect.
At any rate, password managers still help in those cases. If nothing else, for providing a safe place to record what your password is for when you forget it because of the dumb requirements.
I always wonder if such choices come from incompetent IT, or if IT wants to do things better but is banging their heads against corporate owners who think “more hassle = more secure”.
Must be changed every month, can’t use a previous password, AND, for some fucking reason, can only contain 8 characters.
And if you forgot your password, you can call IT and they’ll just read it to you because they have them all saved somewhere.
That was a great place to work at.
Still frustrating. I generally try to make my passwords all lowercase in case I need to type them (especially on a phone). But a lot of places don’t allow that.
deleted by creator
If I’m typing on a computer keyboard, typing words is easier than random letters, but on a phone it doesn’t make much of a difference. What I end up doing is typing my passphrase into my password manager on the computer, and then typing the password on there into my phone.
I do have a password manager app for my phone, but then I have to type the whole passphrase into it so I don’t use it unless necessary.
My favorite, though, is:
types in password “Password incorrect” goes to reset password “please enter a new password” types in password “your new password cannot be the same”
That just means you entered it wrong the first time.
i have had this happen on some websites occasionally while using my password manager.
Sometimes it means the page checking the password is following a different ruleset eg. the main page is case sensitive and the change password page isn’t. Sometimes it’s stuff like the entered password is silently truncated to a fixed number of characters and because of that won’t let you log in. Sometimes it’s wierd character expansions being passed directly to the password checking routine (& or similar).
It often means that one could have derived the correct password from the set of rules - but those rules are not shown when asking for the old password
Exactly this. I want to normalize showing the password requirements when you don’t immediately get the password - if you made me jump through hoops the first time, at least remind me what they were!
I too love the Password game! Please save Paul! ~I truly care about him!~ Truly!
(Sorry, I sometimes like to post really bad comments…)
Haha this is great, got to the chess part before giving in

Same. My country was Jordan. Took way too long to figure out, because it dropped me in the middle of an empty amphitheater with no visible road signs, license plates, etc…
Sorry, you must have a special character. Oh... Not THAT special character, it has to be a special special character, that one isn't valid. Ah, no, that one's too long. It should be shorter. It needs to be between 11 and 11.5 characters.Half the time I now just enter random nonsense until it lets me create an account. Then, when I want to access a website/app again, I just ‘forget’ my password and reset it to some other random nonsense.
Fifty fucking cabbages, the 2023 version
My cabbages!
Here is an alternative Piped link(s): https://piped.video/zRFDr8Vgp_Q
Piped is a privacy-respecting open-source alternative frontend to YouTube.
I’m open-source, check me out at GitHub.
Thanks for introducing me to Piped!
As a hamster enthusiast, I approve of each password provided by this user.
My absolute favourite is when your password is too long but they don’t tell you that, I guess because they weren’t expecting it. It only causes a hitch when you later try to login and it doesn’t let you …
Sorry, that password is already in use
BIG red flag. Abort. Abort.
Also I love when they only support certain special characters. So the psuedo random noise created by my password generator won’t work until I curate out the unsupported characters.
I was changing my password on a pretty big company website the other day.
The password generated by my password manager kept giving me a http error (500 I think)
I generated a new password and deleted all the special characters other than the obvious ones. Boom, worked first time.
So looks like someone is not sanitising their inputs properly.
I sent them an email so hopefully they will fix.
I sent them an email so hopefully they will fix.
One can only hope. But based on my experience, they usually do not. I once sent an email to Microsoft telling them that their Microsoft account app had a vulnerability, and I even sent them the XML line they needed to add to their Android Manifest to fix it, and they wouldn’t do it because it required physical access to the device to exploit. I mean, that’s fair enough, but it was literally one line of code to plug the hole.
They eventually did add that line about 6 years later.
It boggles sometimes.
I remember about 2015 (?) In the vicinity anyway, PayPal has a 12 character MAXIMUM on their passwords.
PayPal, you know the place where you can literally transfer all the money. A 12 character MAXIMUM
I emailed them to suggest they change this requirement. And they replied saying that 12 characters was sufficient if you used special characters and numbers.
Glad they have finally changed it now.
My bank has an 8 character limit. Not minimum, limit
deleted by creator
The worst one is when it only supports up to like 16 characters but doesn’t tell you so it will only use the first 16 characters and ignore the rest. The next time you need to enter it and get the 64 character password from your password manager it will just say it incorrect and you’re left with no idea on why it’s wrong.
I can do you one worse.
My banking app password was not case sensitive for many, many years. They finally fixed it a few years back though!
deleted by creator
Holy shit you might have just explained why I have to reset my password every time for a local fast food joints own website
This was me on a bank’s site till I clued in that I need to shorten my password.
So secure even you don’t know the password. It’s like built in MFA.
Why do you have an account for your local fast food joint?!
so he can get even faster food? idk
To order through their site, I try to use the places own sites instead of justeat etc so they get more of the money. As you can imagine they aren’t the best websites though.
You can’t just order per telefon?
Fuck. I gave it a try for real this time and hit a permanent game over condition.
spoiler
Apparently you can overfeed Paul
Darn, I wanted to see what came next. Some of those rules were hilarious. But I’m not doing that all again.
That was my limit too!
Had to give up at rule 20 because I was using a phone.
Spoiler
As much
funpain as that was, highlighting with a touch screen is nowhere near fast enough to put out the fire.Would love to see a speedrun leaderboard for this, though.
I got to the “wordle” one before giving up. jesus lol, nice meme
It was crone btw.
wow, spoilers /jk
Password can’t exceed 32 characters
Garbage
You think that’s bad, a decade ago I had to use a government-run website that required passwords be exactly 8 characters
i wouldn’t even mind if it was 32. 32 is a damn strong password.
I’ve seen as low as 10 digits in the past
My Wells Fargo password used to be max 8 characters, and when you use the phone you you can basically use the keypad to log in.
So it’s basically 8 DIGITS
Wow, super secure!
32 is a damn strong password
Not necessarily: only if it’s generated properly, and only for the moment - that will change in the next few years.
You do realize that length and symbol type are only 2 out of many other factors that go into a strong password?
Ok, fair, not all 32 digit passwords will be secure.
11111111111111111111111111111111 is not secure, but I was trying to imply, in a properly generated password, 32 digits long is very secure.
but I was trying to imply, in a properly generated password, 32 digits long is very secure.
I understand, and I think you make a valid point as far as the discussion is concerned.
It’s unfortunately still a little more complicated than that, though.
Like I said, there’s more to a password than length and symbol type.
Even something like cF*+@aXbIdFHje2vZiU-1 is less secure than if it were generated by a good PRNG.
D0@ndro!dsDr@3@m0f3l3ctr!cSh33p? is also insecure, though it might have been considered secure 4-5 years ago.
You see what I’m saying?
Then of course there’s hash algorithms and how those are used to authenticate the passwords themselves, etc.